Cyber Security
Protect your data wherever!
cyber security
The Environment
Your business data is everywhere in today’s interconnected and complex digital supply chain.
It is shared with suppliers, partners, cloud platforms, third-party applications, IoT, and more.
Protecting your data is not solely in your own hands but relies on numerous third parties. Unfortunately, security threats are growing exponentially, with over 50% of data breaches affecting SMEs. Cybercriminals are increasingly conducting targeted attacks.
The Risks
A data breach can lead to business failure, significant financial losses, heavy fines, and a severe blow to your business reputation.
Customers are now more sensitive to business data breaches. Ensuring their privacy and data security is vital to maintaining customer trust in your business.
Our Mission Your Protection
RBL’s Cyber Security services provide complete data protection coverage, from infrastructure planning, prevention, control, threat, risk monitoring, and awareness to security breach response and investigation.
Leveraging our experience and expertise combined with our innovative technologies and international practices, all your needs are fully covered.
WHAT WE OFFER YOU
Supply Chain Risks
More…
Digital Risk Protection
More…

Information Security Awareness
More…
Data Security
More…
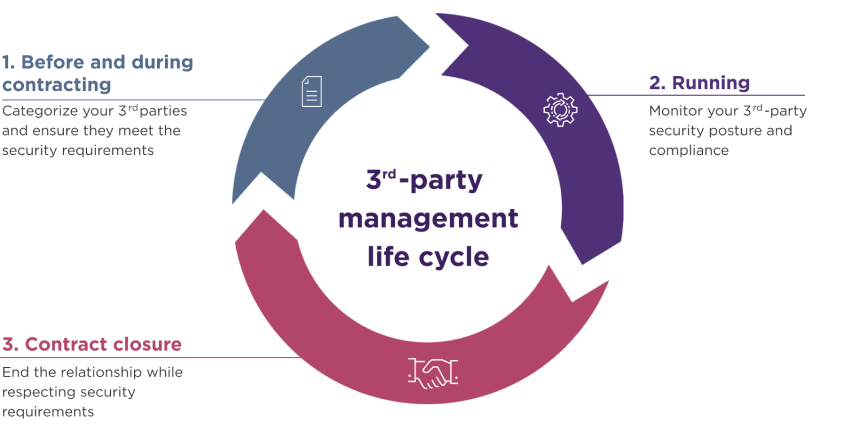
Supply Chain Risks
Every member of the supply chain transmits a risk to your Business.
Effective management of suppliers, providers, partners, etc., to identify and limit potential threats and risks to ensure the best possible operation of the supply chain. You need to trust your data to make decisions based on it.
For any cooperation, you must:
- when choosing partners is necessary a complete cyber risk assessment
- ensure that the terms of the contract are clearly defined and that all contractual obligations are documented
- frequently checks on compliance with the obligations
- continuous monitoring for identification of upcoming threats and risks
At Rethink Business Lab, we offer complete solutions to eliminate the weak links in your supply chain.
Supplier risk assessment
Signing of a suitable contract
Regular supplier evaluation audits
Constant updating
Digital Risk Protection
In partnership with cybersecurity company Skurio, we provide a digital protection platform that automates searches across the surface, deep, and dark web finding the exposure of critical business data and potential cyber threats for businesses of all sizes and industries. We cover multiple types of threats, about domains, including fake URLs, compromised user accounts and emails, confidential information, financial data, IP addresses, keywords, and more.
Look beyond and out of your network using Skurio, monitor risks from third parties, and upgrade your cyber defenses.
Breach Alert
More...
Monitor external threats and breaches by providing instant alerts—Automate manual processes, saving time and effort.
Dark Web Monitoring
More...
The automated Dark Web Monitoring service is atthe Skurio Digital Risk Protection platform. It performs scans of the Surface, Deep and Dark Web around the clock to expose your business data, effectively identifying threats and risks.
Domain Monitoring
More...
Protect your business from phishing attacks and brand impersonation by locating false domains that collect customer data or spread malware.
Cyber Threat Intelligence
More...
It aggregates real-time cyber information that combines multiple surface, deep, and Dark Web sources into a single data stream, providing great search and analysis capabilities.
Cyber Threat Intelligence Services
More...
The threat analyst team offers continual expertise through an information services package tailored to your needs or to provide support during specific breach response situations.
Integrations
More...
Our platform’s capabilities can be integrated into your security operations or IT security apps through open APIs and application links.
Don’t stay in the dark. Find out how exposed you are to digital risks



Information Security Awareness
- 97% of users cannot recognize a well-written phishing email
- 91% of cyberattacks are carried out via phishing emails
- Financial fraud exceeds €500 billion
If your staff can promptly detect and address attacks, reduce severe threats and risks.
Everyone who uses a computer or mobile phone should learn how to avoid falling victim to online attacks through emails or SMS.
A continuous interactive training program helps your staff to be informed and aware of the risks of current threats and attack methods.
In partnership with Attack Simulator, we revolutionize your staff’s digital security practices.

Automated cyber attack simulations
More...
We simulate phishing attacks, social engineering, and malware intrusions.
Real Phishing attack
More...
Through realistically designed web pages, we test user vulnerability involving extracting personal and business-related information.
Analysis of user behaviour
More...
We collect user data and compile it into detailed reports, giving you details of your business’s digital security awareness.
Educational platform
More...
In Greek and other languages
Multimedia lessons.
From extensive articles to engaging videos, they keep their attention on the ATTACK Simulator educational platform.
Elaborate quizzes
Test your cybersecurity knowledge and try the interactive quizzes at the end of each lesson.
Practical guides
Each lesson includes practical handouts designed to help users learn the basics of cybersecurity.
Monitoring progress
We provide an overview of how users can cover the available content.
Training by trainers
More...
Our experienced trainers will implement the appropriate training specifically for your business needs. The training takes part on-site or online.
Permanent Support
More...
We offer comprehensive support, including platform setup, pre-markups, result analysis, and improvement recommendations.
Compliance with Regulations
More...
Digital security awareness training is a necessary requirement for regulatory compliance and security-related certifications, such as GDPR, ISO/IEC 27001, PCI-DSS, and HIPAA, particularly for data protection.
Train your staff not to “bite”

Data Security
We offer a comprehensive range of services to enhance the overall effectiveness of information security within your business.
From infrastructure design, security auditing, certification, training, investigation, and incident response, our partners help you operate in an environment ready to deal with threats and risks.

Cyber Security
IT Assessment and Consulting
Vulnerability Assessments
Penetration Tests
Risk Assessment
Disaster Recovery & Continuity
Security Incidents’ management
ISO 27001 Security standards and certification
*Απαραίτητο πεδίο
